API Security Project Identifies Top 10 Vulnerabilities
by Amit
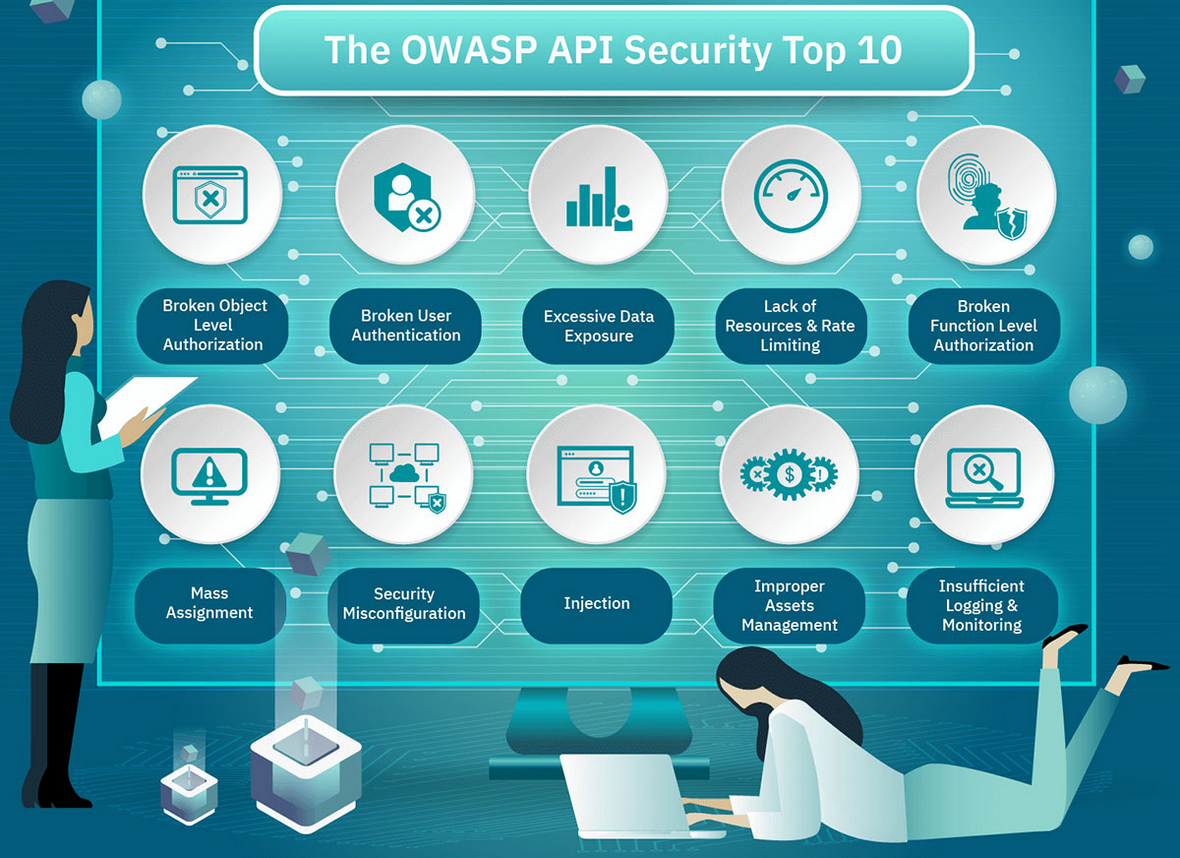
The primary API vulnerability that exposes organizations to potential data breaches is identified as “broken object level authorization,” as stated in a report from the independent Open Web Application Security Project (OWASP). According to the OWASP API Security Top 10 report, attackers can exploit this vulnerability by manipulating the ID of an object within the API request, potentially leading to unauthorized access to sensitive data. The report emphasizes that this issue is prevalent in API-based applications, where the server component often relies on parameters like object IDs sent from the client, without fully tracking the client’s state.
The consequences of such an attack are severe, posing risks of data loss, manipulation, and even a complete takeover of the system. The report underscores that developers play a crucial role in defending against this API vulnerability, emphasizing the need to implement object level authorization in the code. Proper coding practices are essential to ensure that only users with the correct permissions can access and take action on requested objects.

If developers overlook setting up API authorization and access control mechanisms correctly during development, the vulnerability becomes an open door for attackers. Access control detection, as per the report, is not easily automated through static or dynamic testing, reinforcing the importance of getting it right from the code level.
To illustrate the potential impact of an API breach, the report provides a scenario involving an e-commerce platform. The attacker, by manipulating API endpoints, gains unauthorized access to sales data from numerous online stores, showcasing the severity of the broken object level authorization vulnerability.

OWASP offers a set of recommendations for development teams to safeguard against this vulnerability, including implementing proper authorization mechanisms based on user policies, avoiding the use of client-sent IDs, using authorization mechanisms to validate user access, preferring random and unpredictable values for record IDs, and thorough testing of the authorization mechanism.
Erez Yalon, Director of Security Research at Checkmarx and co-leader of OWASP’s API Security Project, highlights the significance of addressing API security risks, noting that APIs pose a security risk that is not always fully recognized. The OWASP API Security Top 10 serves as a guide to help developers identify and prevent vulnerabilities in their applications, offering mitigation recommendations for the identified top 10 API vulnerabilities.
The primary API vulnerability that exposes organizations to potential data breaches is identified as “broken object level authorization,” as stated in a report from the independent Open Web Application Security Project (OWASP). According to the OWASP API Security Top 10 report, attackers can exploit this vulnerability by manipulating the ID of an object within the…
Recent Posts
- Unveiling the Winning Strategy: The Intersection of Web Design and Sports
- Microsoft Acquiring JavaScript Dev Platform npm, Will Integrate with GitHub
- Javalin Framework for Kotlin and Java Updated
- API Security Project Identifies Top 10 Vulnerabilities
- .NET-Centric Dev Tooling Vendor Boosts Blazor Components, Supports .NET Core 3.0